Acoustic Attack : The Unseen Threat
As the digital landscape evolves, so do the methods employed by cybercriminals. In this era of connectivity and reliance on technology, a new breed of cyber threat has emerged—one that exploits sound waves to steal sensitive data. The “New Acoustic Attacks” has sent shockwaves through the cybersecurity community, boasting an unsettling accuracy rate of 95%. In this article, we delve deep into the mechanics of this stealthy attack, exploring its potential implications and offering insights on safeguarding against it.
Understanding Acoustic Attack
The Subtle Symphony: A Prelude to Data Theft
Acoustic attacks, a form of cyber assault, exploit the subtle sound waves generated by keystrokes to extract sensitive information. This ingenious technique leverages advancements in machine learning to interpret sound patterns, transforming them into comprehensible text. These attacks hinge on the concept of sound leakage, where vibrations from typing travel through various mediums and can be captured by specialized equipment.
The Mechanics Unveiled: How Acoustic Attack Work
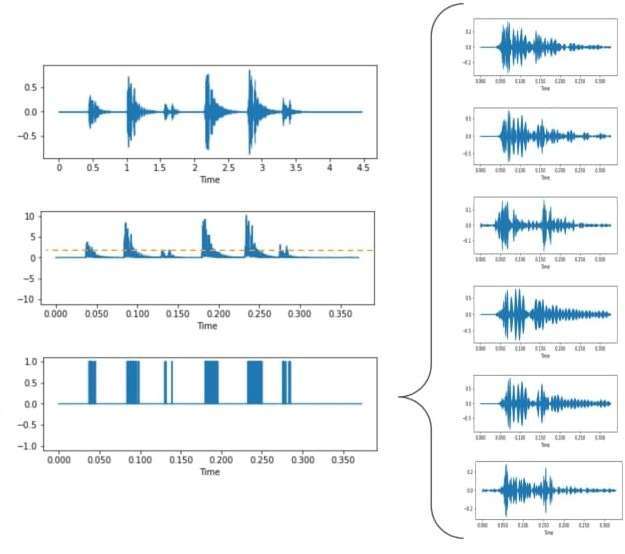
In an acoustic attack, the attacker strategically places microphones and sensors near the target’s workspace. These sensors capture the vibrations generated by typing, converting them into digital signals. Advanced algorithms then decipher these signals into text, effectively stealing the victim’s keystrokes—potentially compromising passwords, sensitive documents, and confidential information. Recent research showcases the remarkable accuracy of these attacks, with success rates reaching up to 95%.
Implications for Cybersecurity and Data Protection
Beyond the Digital Realm: A Physical Breach
Unlike traditional cyber threats that exploit software vulnerabilities, acoustic attacks capitalize on the physical leakage of sound. This makes conventional cybersecurity measures, such as firewalls and encryption, inadequate in countering this unique threat. Organizations must acknowledge this paradigm shift and adopt a holistic approach to protect their data.
Fortifying Defenses: Guarding Against Acoustic Attack
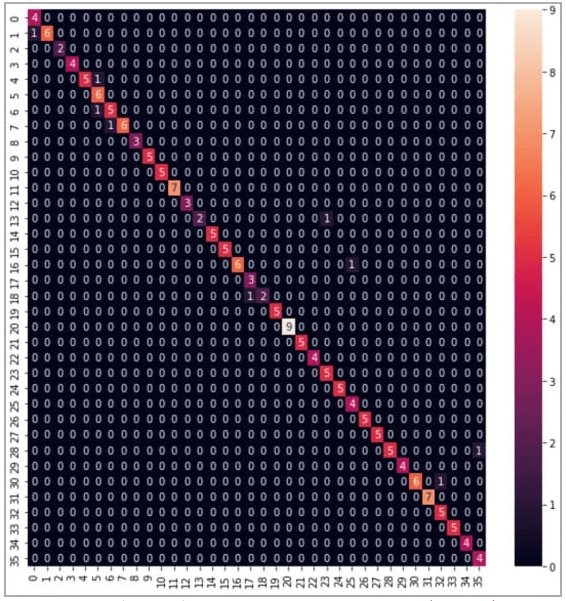
The battle against acoustic attacks requires a multi-pronged defense strategy. Organizations must prioritize the design of secure workspaces, incorporating materials that minimize sound propagation. Moreover, the deployment of sound masking technologies and white noise generators can thwart eavesdroppers by rendering captured sound patterns unintelligible.
Safeguarding Against Acoustic Attack: Best Practices
1. Designing Secure Workspaces
Creating noise-resistant environments through layout adjustments and sound-absorbing materials.
2. Implementing Physical Barriers
Installing partitions and acoustic panels to prevent sound vibrations from traversing beyond designated areas.
3. Harnessing White Noise Generation
Deploying white noise generators to disrupt the clarity of captured sound patterns, reducing the risk of successful attacks.
4. User Education and Awareness
Educating employees about the existence and implications of acoustic attacks, fostering vigilance during typing activities.
5. Advanced Threat Detection
Investing in intrusion detection systems to identify unauthorized eavesdropping devices and unusual sound patterns.
6. Encryption and Data Loss Prevention
While not a direct solution to acoustic attacks, robust encryption and data loss prevention strategies remain integral to overall cybersecurity.
7. Routine Security Audits
Conducting regular assessments to identify vulnerabilities and tailor defenses accordingly.
Navigating the Future: Strengthening Digital Resilience
The advent of acoustic attack underscores the need for perpetual vigilance in the realm of cybersecurity. As technology advances, so do the methods of cybercriminals. By embracing comprehensive defense strategies, organizations can fortify their digital fortresses and mitigate the risk posed by acoustic attacks. In this era of sound-based espionage, knowledge is indeed power.
Frequently Asked Questions
Q: Can acoustic attack be prevented solely through encryption?
Encryption provides an essential layer of protection, but acoustic attacks exploit physical sound leakage. Combining encryption with other security measures is crucial.
Q: How can organizations foster awareness about acoustic attacks?
Organizations can conduct cybersecurity training sessions, raising awareness about acoustic attacks and encouraging employees to adopt secure typing practices.
Q: Are there real-world examples of successful acoustic attacks?
While specific instances are limited, ongoing research emphasizes the feasibility of acoustic attacks, urging us to remain vigilant.
Q: Can white noise generators disrupt office productivity?
When properly calibrated, white noise generators strike a balance between security and productivity, minimizing potential disruptions.
Q: What steps can individuals take to protect against acoustic attacks?
Individuals should practice typing discretion, be cautious in shared workspaces, and stay informed about emerging cyber threats.
Q: How do acoustic attacks compare to other cyber threats?
Acoustic attacks exploit a unique physical phenomenon—sound leakage—setting them apart from conventional software-based vulnerabilities.
Know about: Facebook Privacy Settlement



Pingback: Nepali Hackers reaches on semi-final of HackerOne Ambassador World Cup 2023, defeating American team - Bcapoint
Pingback: Types of Cyber Attacks You Should Be Aware of in 2024 - Bcapoint
Pingback: How to Troubleshoot XAMPP's MySQL Not Running Issue: A Step-by-Step Guide 2023 - BCA NOTES : BCAPOINT